In a variation on the Google forms e-mail spam wave I wrote about in the beginning of the year, cybercriminals are making use of other platforms and online signup forms to circumvent spam filters and spread their malicious links.
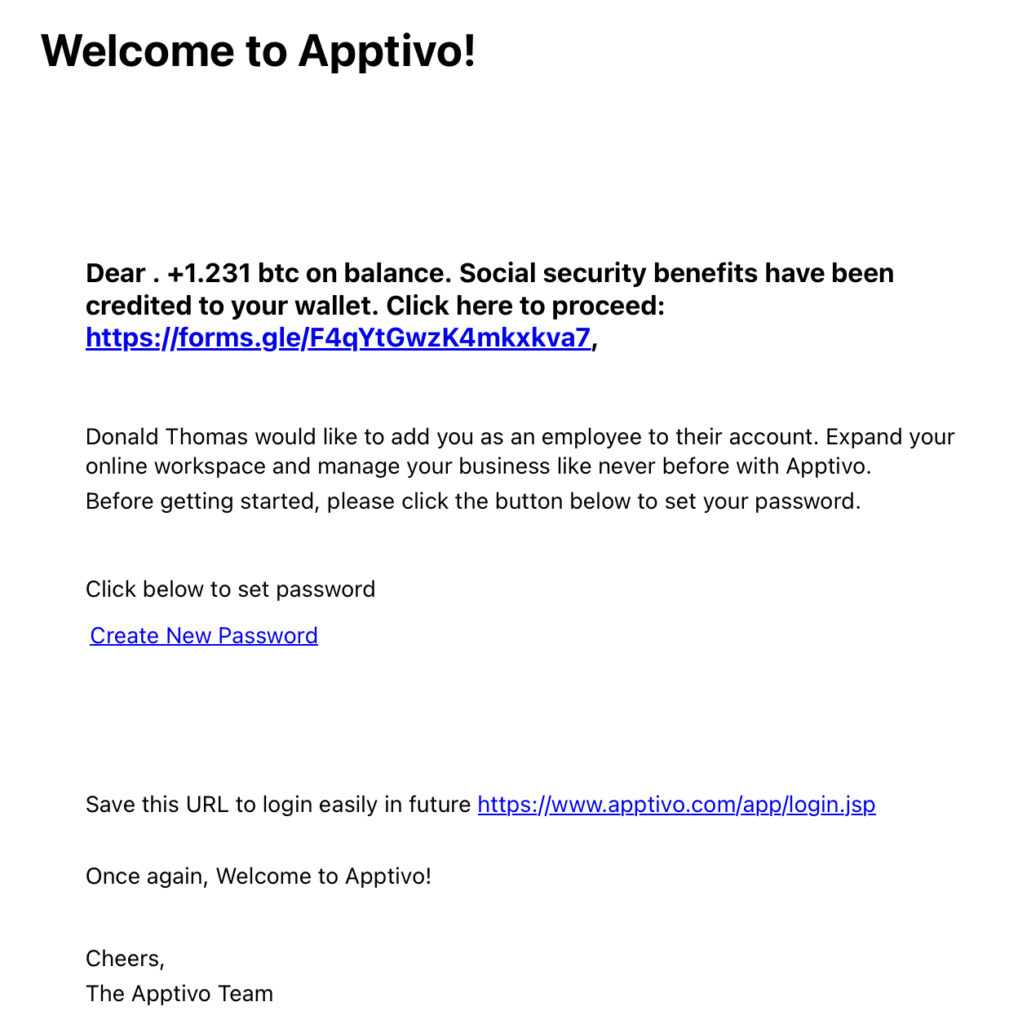
These scammers use a multitude of strategies to make use of legitimate services, domains and webservers instead of their own infrastructure that would quickly get flagged as spam.
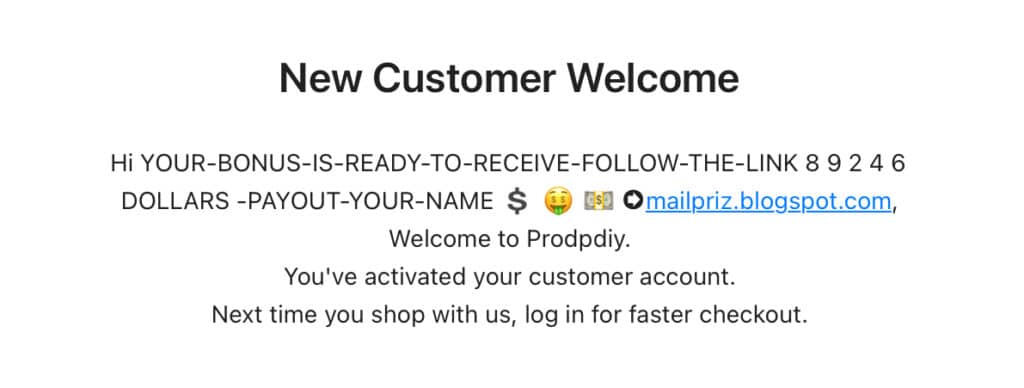
Some of them make use the fact that a substantial amount of websites don’t implement input validation on the “name” field, in the form where users sign up for the web application. Giving criminals the ultimate freedom to take over the content of the e-mail and add malicious urls. This with varying rates of succes…
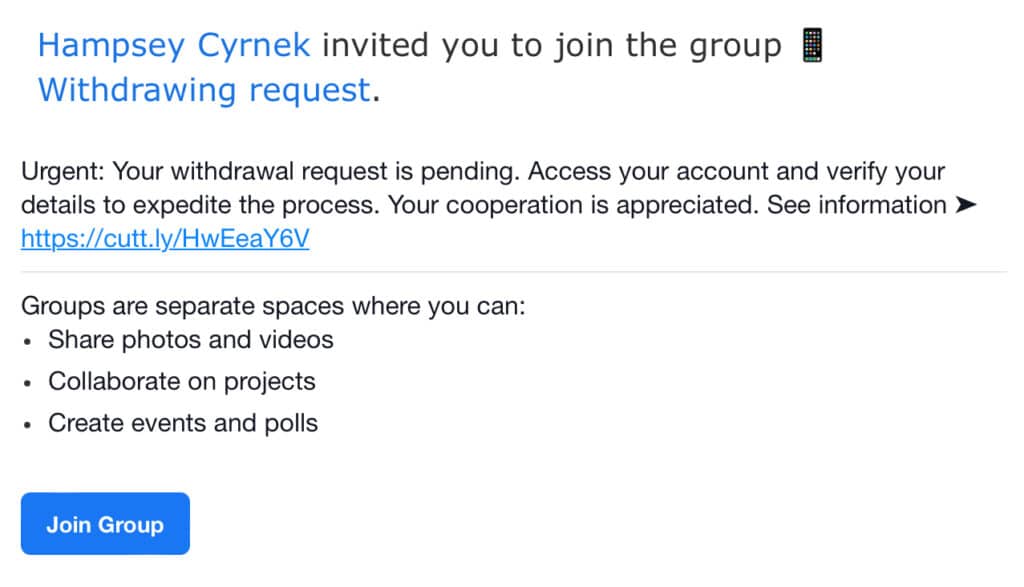
Others make use of legitimate features in web applications that send out invites for groups, or reminder e-mails in project management software. Like this e-mail from Facebook (Meta):
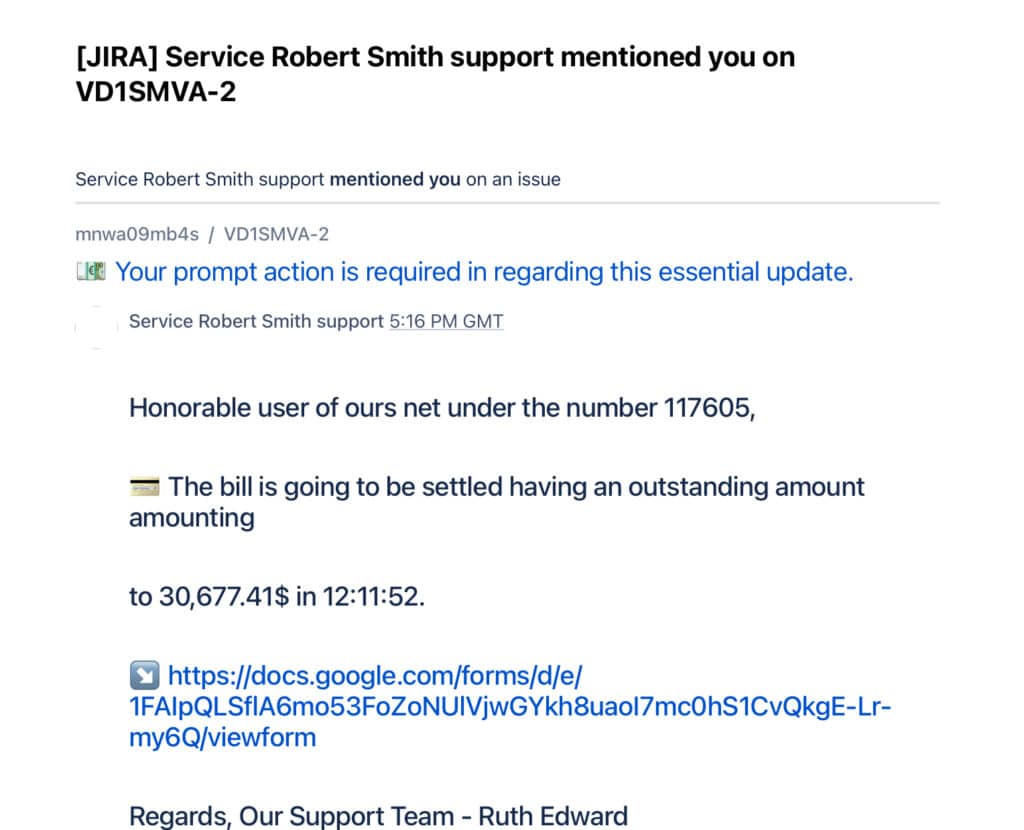
Or this one from Atlassian:
Prevention
While achieving total prevention may be challenging without restricting features for normal users, there are measures to mitigate abuse in your web applications and domains. For the “Name” field, handling input validation for names is complex; consider blocking input containing URLs and domains initially. Implementing rate limits can deter cybercriminals from exploiting features for mass emails to potential victims.
Vigilance is key. Regularly monitor service usage, detect misuse, and promptly deploy countermeasures for the most effective strategy against abuse.